8.1 KiB
| title | description | date | categories | tags | draft | toc | |||
|---|---|---|---|---|---|---|---|---|---|
| I love fucking around with scammers | The skies bless me with a scam message every 6 months or so, and I always tend to mess with the people who's behind them | 2024-08-08 00:00:00+0000 |
|
|
false | true |
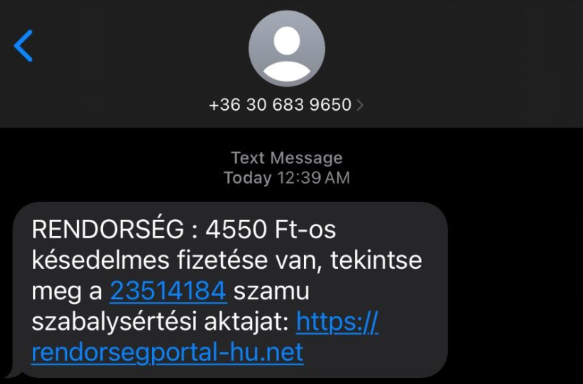
A year ago I got a scam SMS from supposedly the Hungarian Law enforcement saying that I have some payments due and If I don't pay it in time, it will result in legal consequences.
Obviously someone with common senses and a bit of knowledge about the internet as a whole will know that this is likely a scam.
I could have ignored this and went on by my day but then I remembered that my parents always keep asking if what they have received on facebook is a scam or not... Now thankfully my parents have me, therefore they can verify with me if what the person behind those messages is promising really will really happen. But most people are foolish enough to fall into these kinds of traps. Elderly people, those who don't quite understand the shadiness of these and people in the autism spectrum (like my close relatives). And therefore I have decided to flood their servers with fake data.
Building my first spamming script
First I have conducted a basic research. I went to my PC and opened up the developer console in Firefox and entered some fake data into the input fields. Then I analyzed all the requests the website was sending to the server and from that point I got a clue of how to build a basic script that could send millions of fake records.
Talking about fake. I was smart and decided not to spam random data into every field. Instead I choose to fuck with them even more by sending real looking data. This way they have a much harder time deciding what data is real and what is not.
Since the target audience of these assholes were Hungarians I went and got a h u g e list of first and last names and used those databases to generate real looking names. I also used some python libraries to generate all kinds of credit cards. Visa, mastercard you name it. And after about an hour I got a fully working script that could send thousands of record a second to their database.
Running the script
I knew I would get blocked really fast. And I was right, after about 2 000 requests I got IP blocked.
Funny because I wasn't having enough fun yet. I decided to call up a few of my friends and got them to download my script and run it in the background. I also decided to set it up on my VPS and after all that I was spamming them from about 12 IP addresses.
Long story short, after 2 weeks of basically ddos-ing them they took their website down. I win.
A more sophisticated attack
Today I've seen a mutual on a social media platform post a screenshot of them receiving a scam SMS from the hungarian police. Shiver my timbers I must pay them my whole life savings so they don't come and arrest me! Anyways... I have decided to look into that scam as well and have found my self in a bittersweet position. These attackers were using some payment processor behind their servers that would automatically charge the victim a certain amount of money upon entering their credit card details. Now how do I know that you might ask? I don't, It's my best guess.
Now the evidence leading up to that comes like this:
I conducted research as in the first example, and seen that the frontend javascript code was sending requests to telegram. Those requests were the second part of their scam. First you entered your card details, and then they would most likely enter that data into a payment processor that would require some two step authentication to approve the payment.
Also, What the fuck. These idiots really just put their bot's whole api token into their javascript code and sent editMessage commands to their telegram channel. Truly premature system design. But I mean these scammers are the lowest hanging fruits after all, they don't even try. They could have just implemented that code into their backend and I would have had a harder time destroying their legacy.
I copied the whole telegram URL that contained their api key and opened up Insomnia another awesome open-source project ruined by corpos and snooped around. I saw that they only had one channel where the frontend would send the verification code to. They even had fancy buttons added like an ❌ and a ✅ to confirm whether the code was working or not.
[
{
"text": "✔ Code valide",
"callback_data": "yes_tnDmzUe"
}
],
[
{
"text": "❌ Code invalide",
"callback_data": "refait_tnDmzUe"
}
],
[
{
"text": "Code pin",
"callback_data": "codepin_tnDmzUe"
}
],
[
{
"text": "Log bank OTP",
"callback_data": "lb_otp_tnDmzUe"
}
],
[
{
"text": "Banque non pris en charge",
"callback_data": "npc_tnDmzUe"
}
]
After this I started writing my code.
The program
Now this was more complicated, since I would have two factors to align next to each other to convince those idiots that they were really getting people to give away their information.
I wrote a basic rust program that would spawn 1200 threads each with timers at random x seconds that would send random card details to their backend, wait a little bit and then send a dummy text to their telegram channel so they would think they are receiving confirmation of actual codes coming thru.
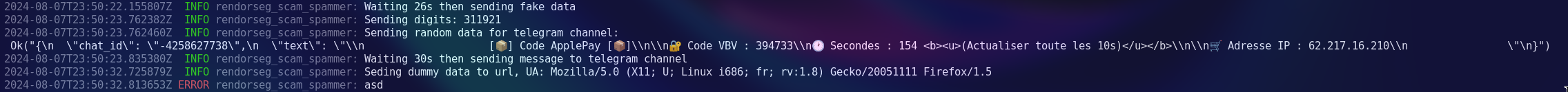
This is how that message looked like:
[📦] Code ApplePay [📦]\n\n🔐 Code VBV : 123456 \n🕐 Secondes : 150 <b><u>(Actualiser toute les 10s)</u></b>\n\n🛒 Adresse IP : 192.168.1.1
Now after all that I would let it run for a few hours and I sometimes tried to snoop into their channels with the bot but telegram is so shit they don't allow bot's to view chat history. You can only do that with an api request that pulls the NEWEST data off the channel and then the client would store it. another reason why matrix is better.
A few hours passed. I was getting bored so I decided to send them some surprising messages. I won't disclose what I've said but lets say it was more than vulgar. I was having a bit of fun. After 4-5 messages they deleted their channel. And soon after that their website got placed into a placeholder login page.... But it was not over...
I made some errors while spawning threads and it resulted in not sending any requests. So all I basically did was make them panic and delete their channel. The next day, I got up and seen that my IP address has changed, thanks ISP and went on the site once more to see if they have done anything. And those fuckers actually did something. They removed the part where they would send the verification codes on the frontend and implemented it into their backend. Now I sat down once more and make some touchups on my code and It started working. After about 5 minutes or so I got IP blocked once again, so I called up a few of my friends.
Since all my friends use windows I had to compile my code to an exe so they could have a chance running it.
Eventually I got a few of them to run it but not as much as the first time. In about 1-3 minutes they would get blocked or get an 404 error. These scammers were active and blocked anyone that would start spamming. In times like this I wish I had a botnet. I lost. But I managed to at least send them a few hundred records.
Lessons
I won't say I'm a genius, anyone with a basic knowledge of HTTP, API's and a bit of programming could do all this magic. What I'm trying to say is that these people really think they could get away with all this. And they really do sometimes. They are probably smart enough to buy their servers with some untraceable cryptocurrency and then deploy their skimming services with fake names. There isn't really a way to stop them. But there is a way to mitigate their impact by sending them a lot of fake data :)